[AWS-CPE] Security
Introduction
In the AWS security overview, the focus is on the shared responsibility model, which is a fundamental aspect of managing security within the AWS Cloud. In this model, AWS is responsible for securing the cloud infrastructure, including data centers, hardware, and software layers. On the other hand, customers are responsible for securing the workloads they run on the AWS Cloud. This division of responsibilities is designed to ensure comprehensive security both in the cloud and of the cloud. We also hints at discussing further security services, mechanisms, and features provided by AWS to enhance cloud security in subsequent sections.
Shared Responsibility Model:
Objective
- Explain the benefits of the shared responsibility model.
- Describe multi-factor authentication (MFA).
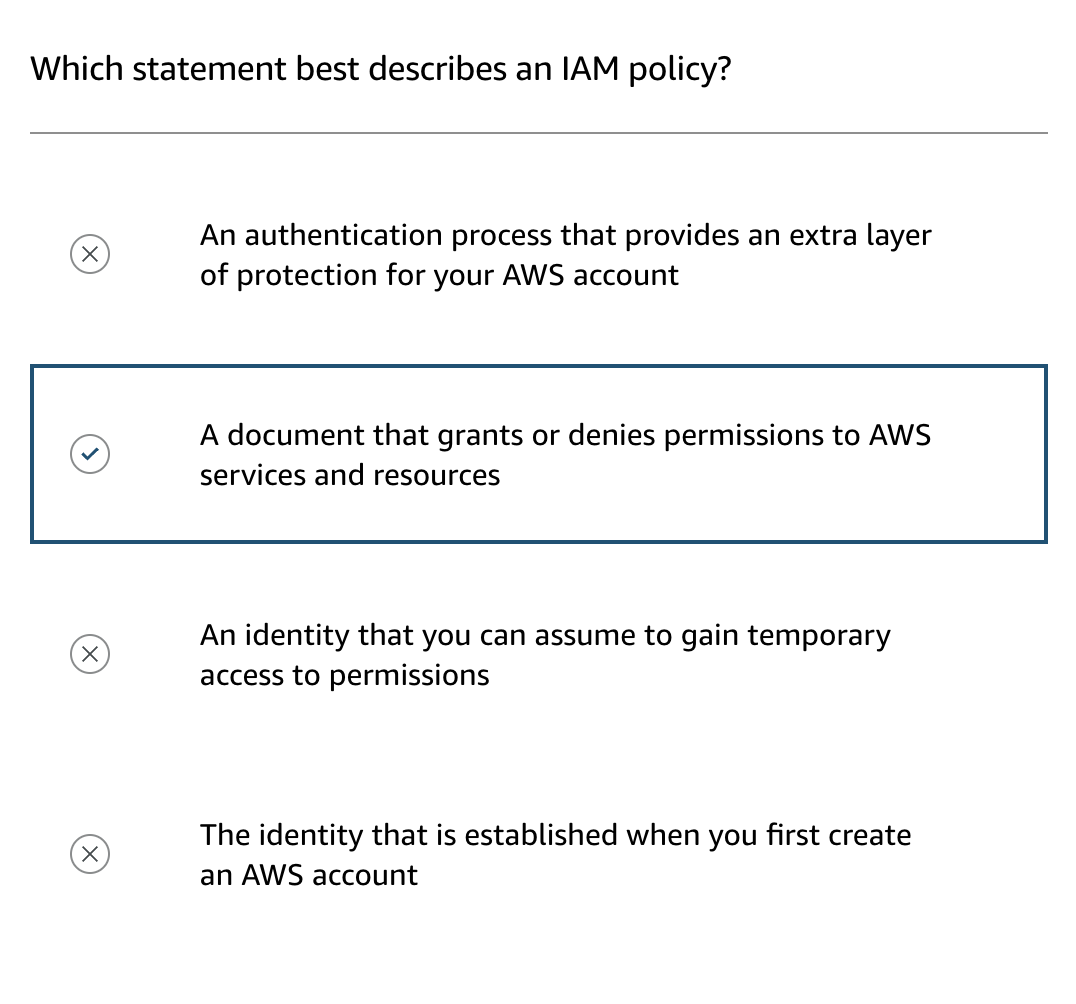
- Differentiate between the AWS Identity and Access Management (IAM) security levels.
- Explain the main benefits of AWS Organizations.
- Describe security policies at a basic level.
- Summarize the benefits of compliance with AWS.
- Explain additional AWS security services at a basic level.
AWS Shared Responsibility Model
In the AWS security model, responsibilities are clearly divided between AWS and its customers through the Shared Responsibility Model, ensuring effective security on both sides:
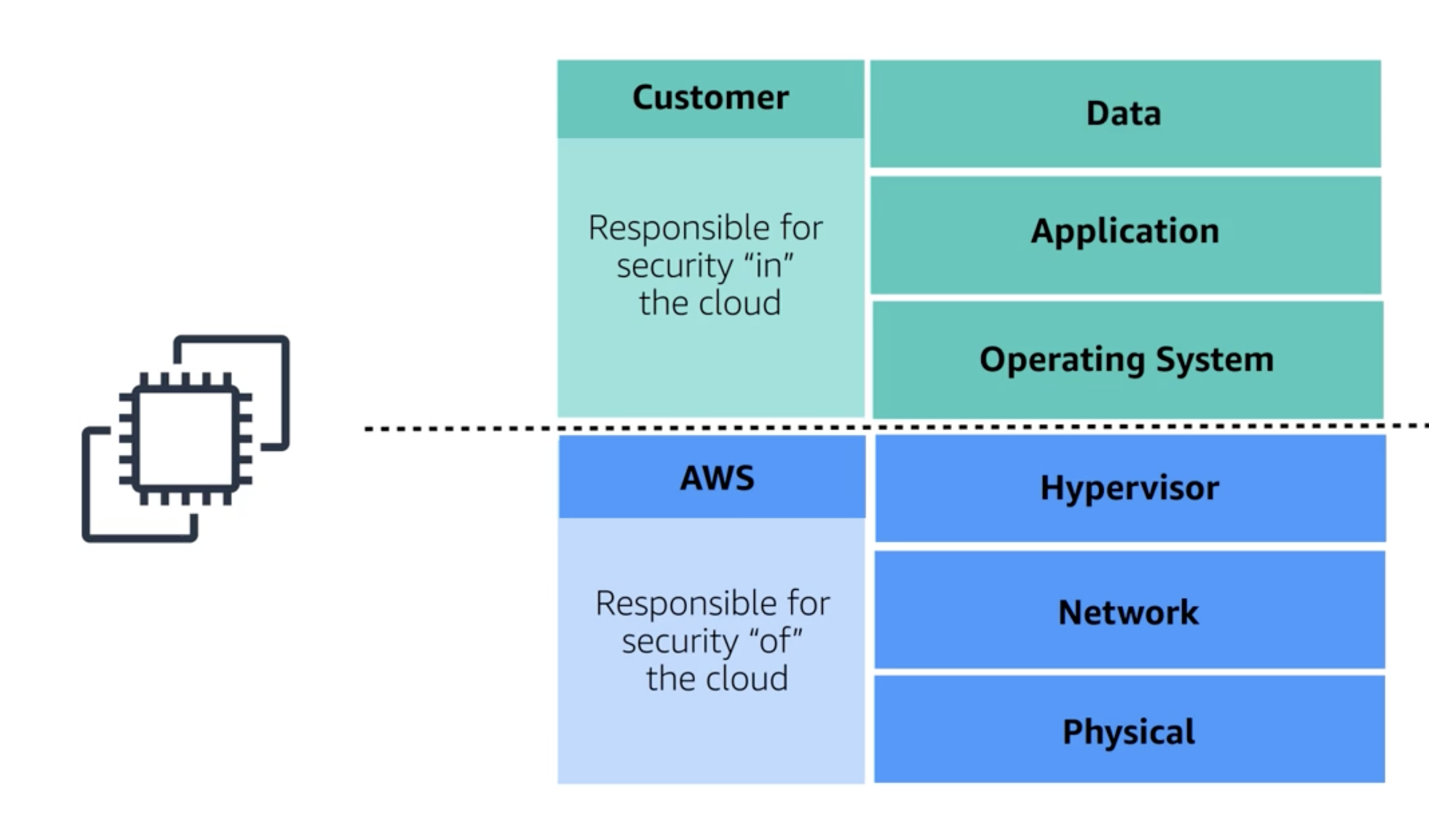
AWS Responsibilities: (‘of’ the cloud)
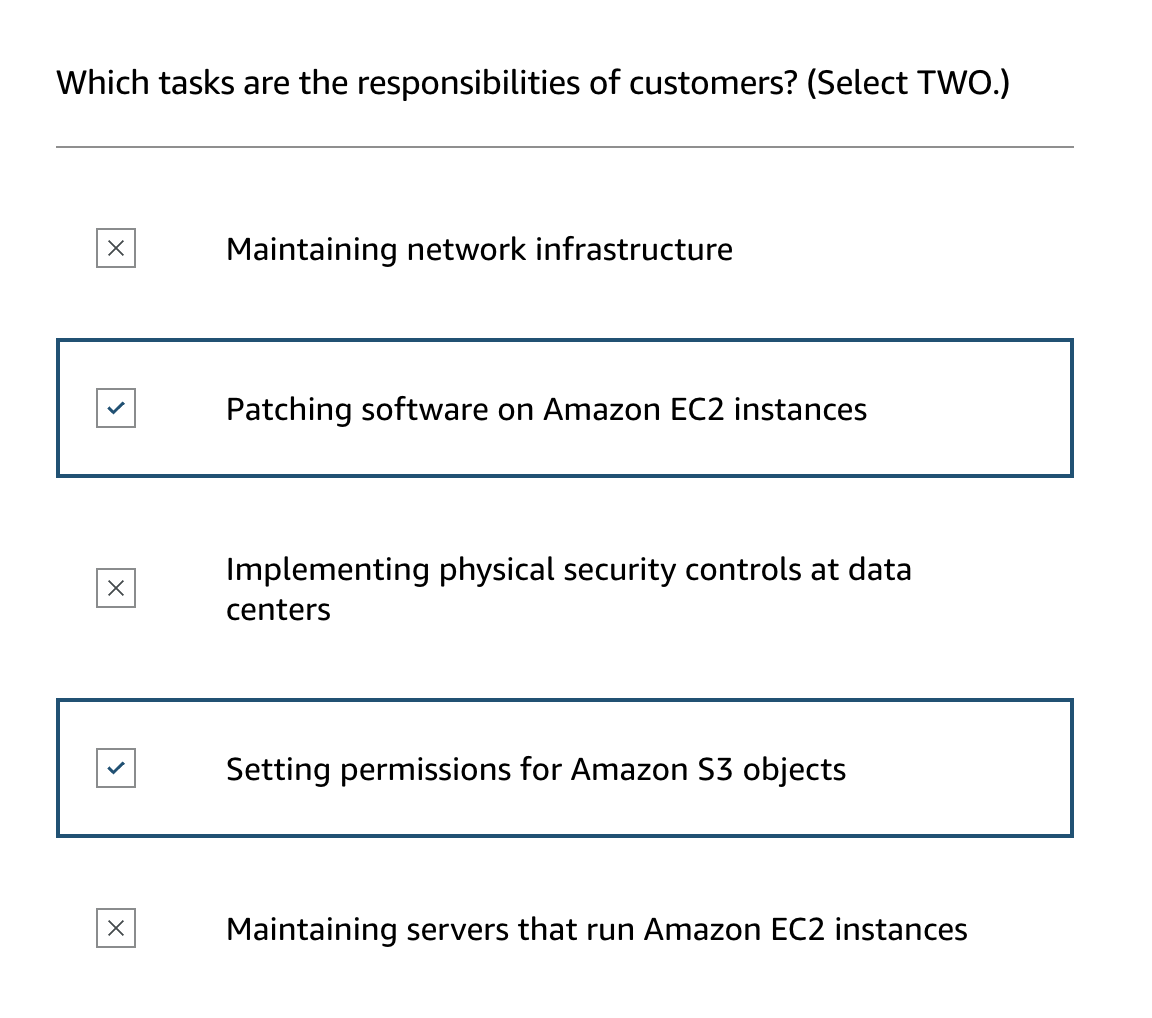
- Physical security: AWS secures the physical infrastructure of the cloud, including data centers, hardware, and foundational cloud services like network and hypervisor.
- Infrastructure management: AWS handles the security of the cloud infrastructure and reinvents technologies to enhance security and efficiency, validated by third-party audits.
Customer Responsibilities: (‘in’ the cloud)
- System management: Customers manage and secure their operating systems and applications.
- Data control: Customers have full control over their data. They decide who accesses the data and manage the encryption.
- Patch management: Customers are responsible for keeping their systems patched and updated.
Division of Responsibility:
- The boundary between AWS and customer responsibilities is the operating system level. AWS secures everything below the OS, and customers manage everything above it, including the OS itself.
Security Tools and Compliance:
- AWS provides tools for data security and compliance, allowing customers to set data access permissions and utilize encryption to protect their data, even if breaches occur.
This model ensures that while AWS provides a secure infrastructure, customers have the autonomy and responsibility to manage their systems and data securely.
Quick Quiz
User Permissions and Access, IAM (AWS Identity and Access Management)
Let’s look at AWS Identity and Access Management (IAM), using the analogy of a coffee shop to clarify how permissions and roles are managed within AWS.
IAM Overview: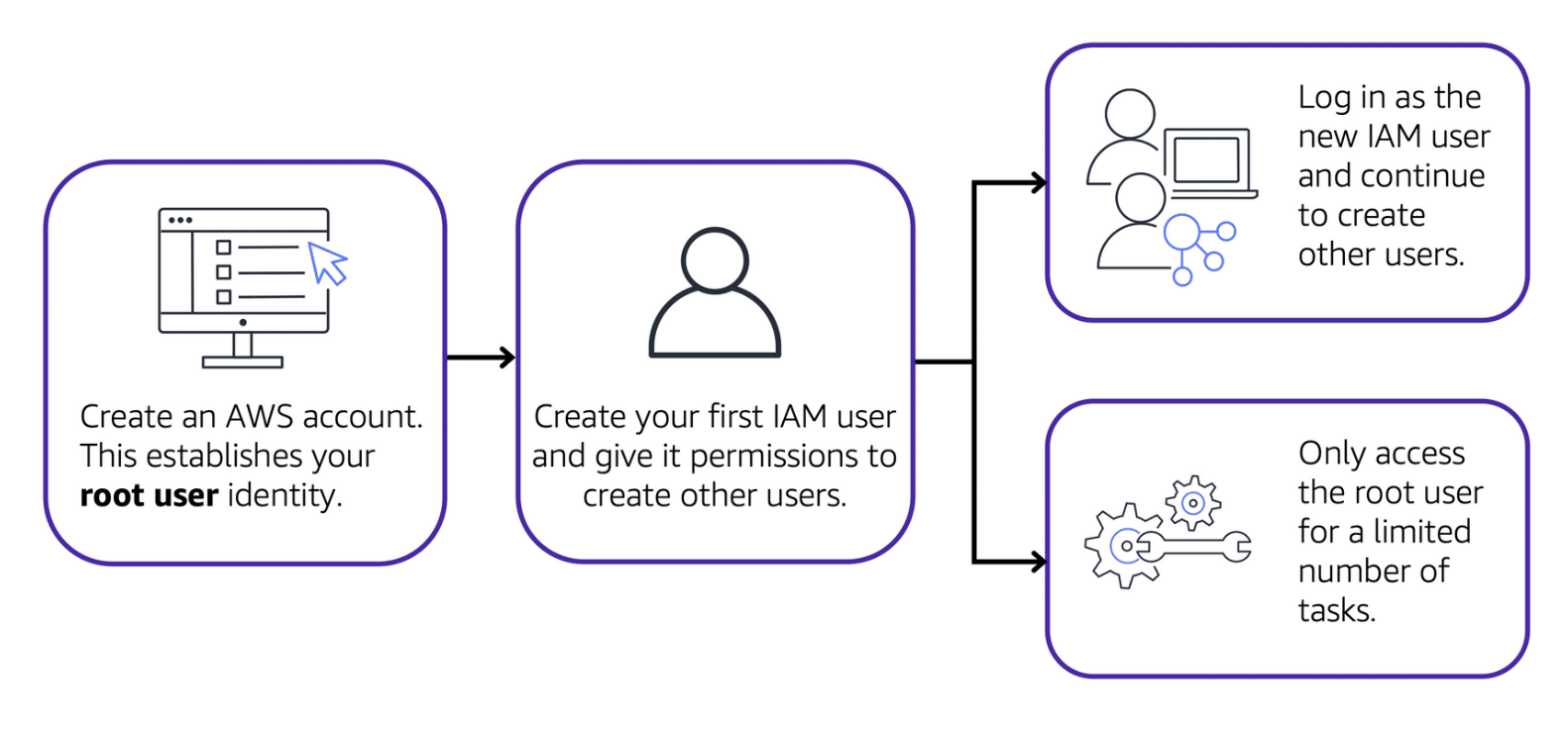
Shared Responsibility
- Security on AWS is a shared responsibility between AWS and the customer.
- AWS secures the infrastructure.
- Customers manage their data and applications.
Root Account
- The root user owns the AWS account and has full permissions.
- Multi-factor authentication (MFA) is recommended immediately upon account creation to enhance security.
AWS Identity and Access Management (IAM)
- IAM Users: Initially have no permissions; specific permissions must be explicitly granted.
- IAM Policies: JSON documents define what actions users can and cannot take.
- IAM Groups: Allow collective permission management for users with similar access needs.
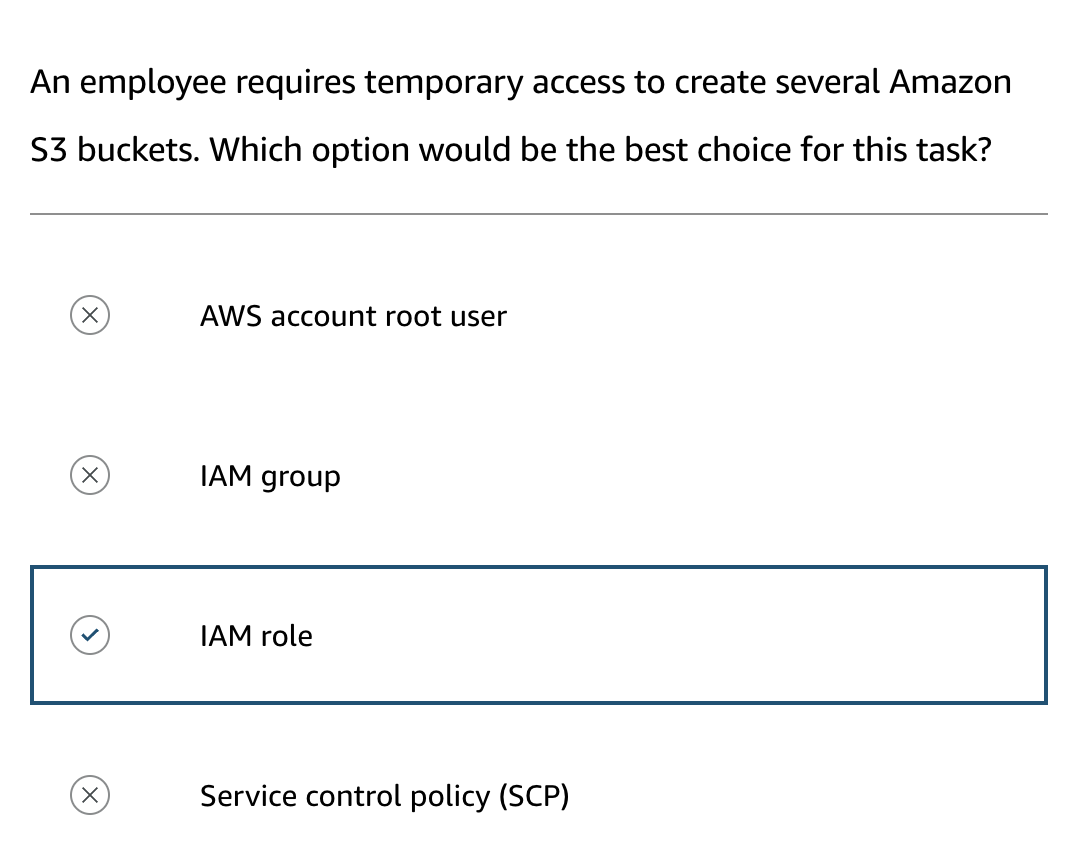
- IAM Roles: Provide temporary access to resources, without needing a username and password, useful for varying daily tasks or external users. (When someone assumes an IAM role, they abandon all permissions that they had under a previous role and assume the permissions of the new role.)
IAM Policy: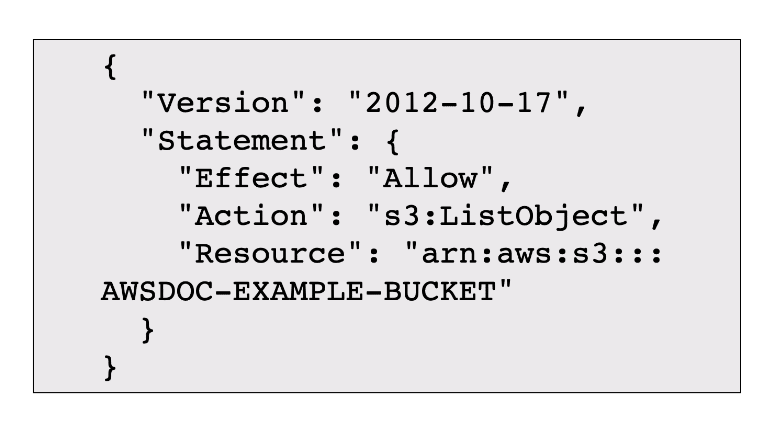
IAM Group:
≈
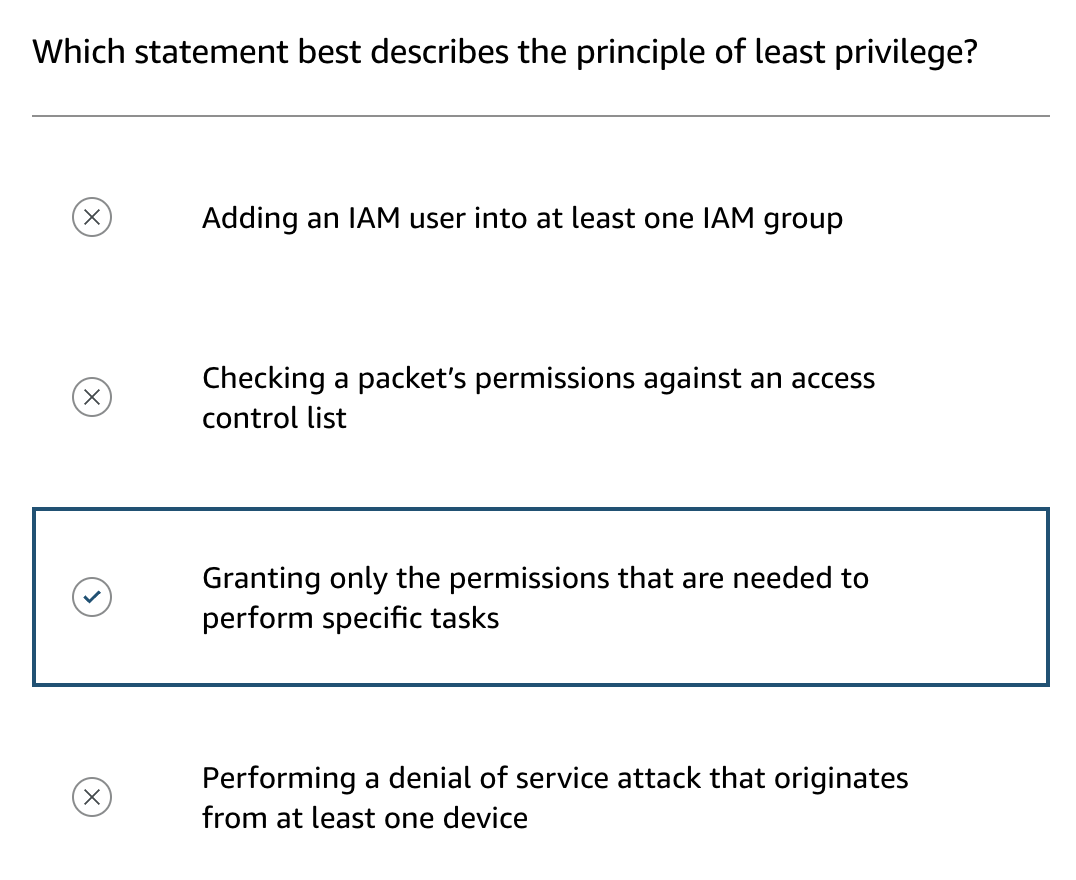
Principle of Least Privilege
- Users should have only the access necessary to perform their job functions, nothing more.
Application in AWS
- Policies control access by specifying allowed or denied actions.
- Roles can be assumed temporarily, mimicking changing responsibilities in a coffee shop, like different roles for staff depending on the day’s needs.
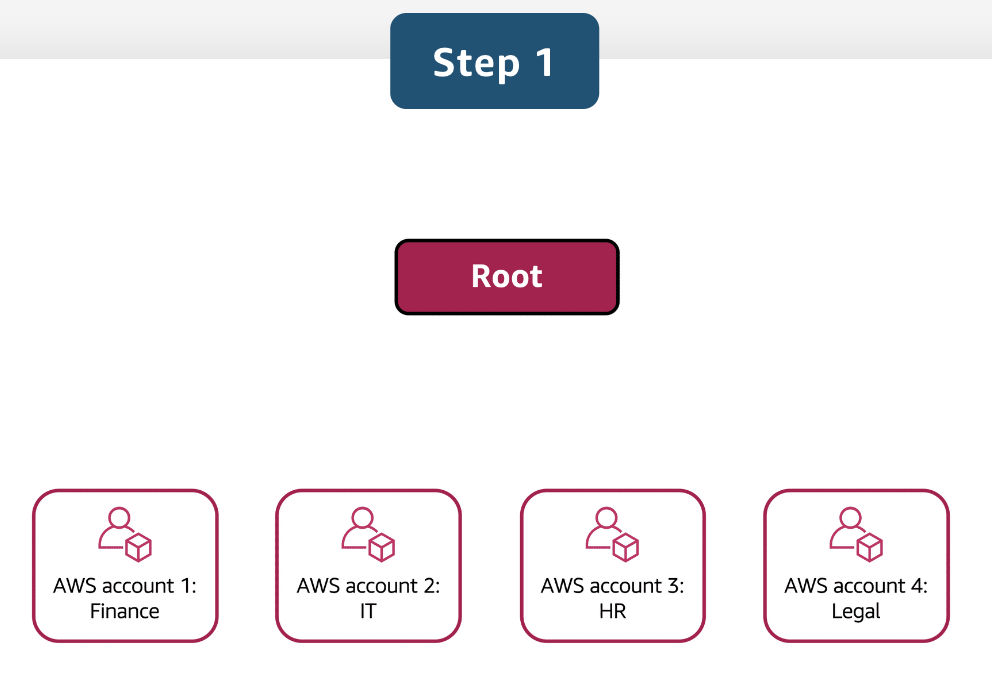
AWS Organizations
As businesses grow and their usage of AWS expands, managing multiple AWS accounts efficiently becomes crucial. AWS Organizations is a service designed to streamline this process by providing tools for centralized account management, ensuring better control over billing, compliance, and security across various accounts. Here’s a concise overview of the primary features and benefits of using AWS Organizations.
Key Features of AWS Organizations
Centralized Management:
- All AWS accounts (e.g., Accounts A, B, C, F, G) are combined into a single organization for centralized governance.
Consolidated Billing:
- One primary account manages billing for all member accounts, enabling easier tracking and payment.
- Bulk discounts are available through consolidated purchases, providing cost savings.
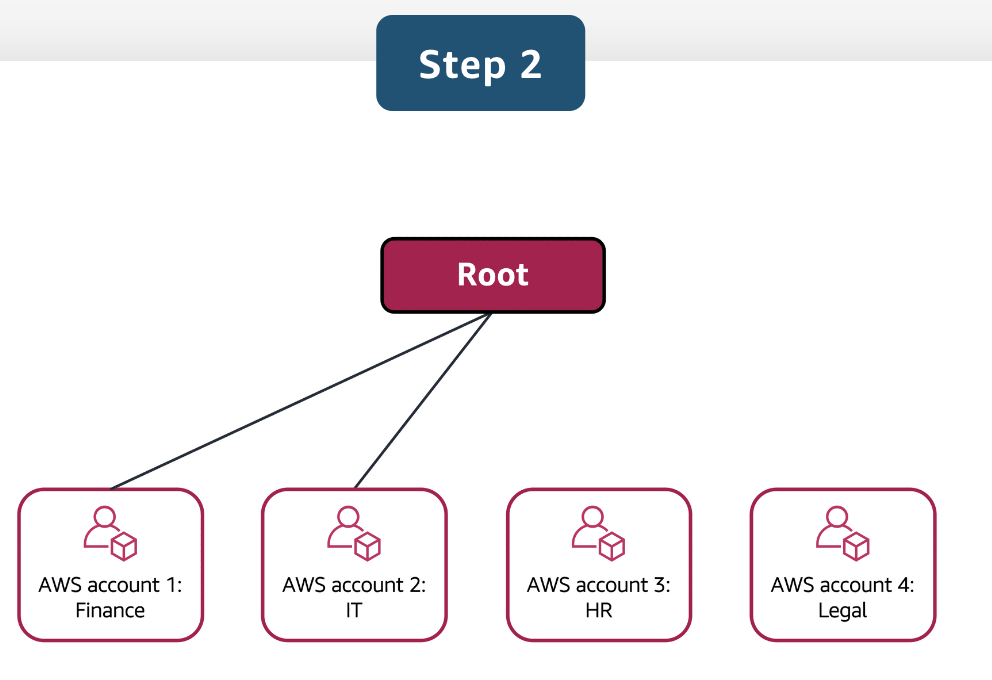
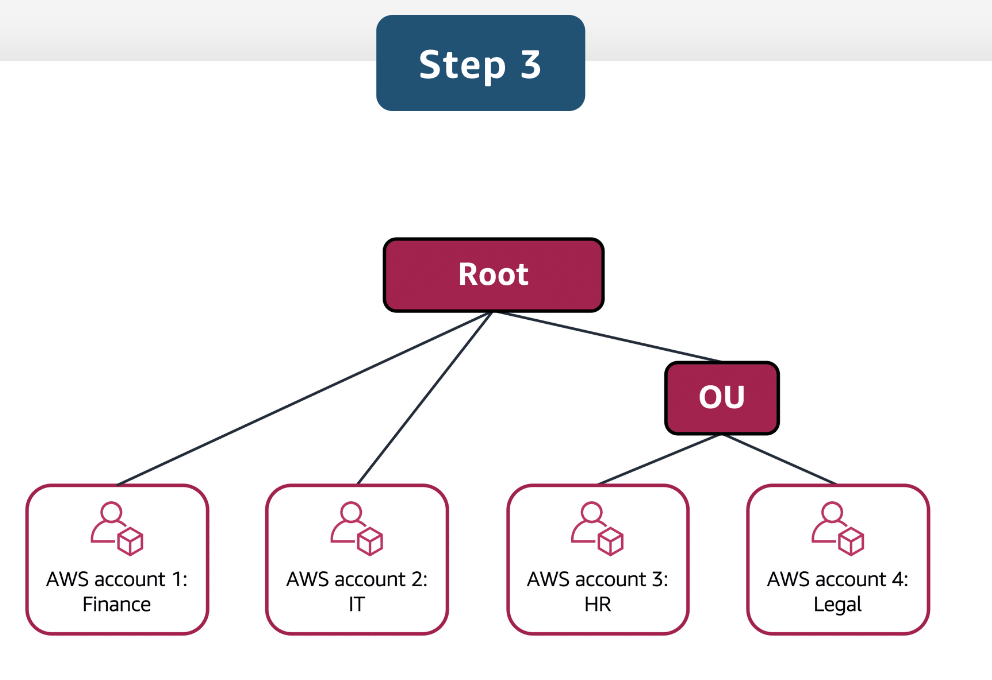
Hierarchical Account Groupings:
- Accounts can be organized into Organizational Units (OUs) based on specific needs such as security, compliance, or budget.
- Examples include grouping accounts by business unit (BUs) or regulatory compliance requirements.
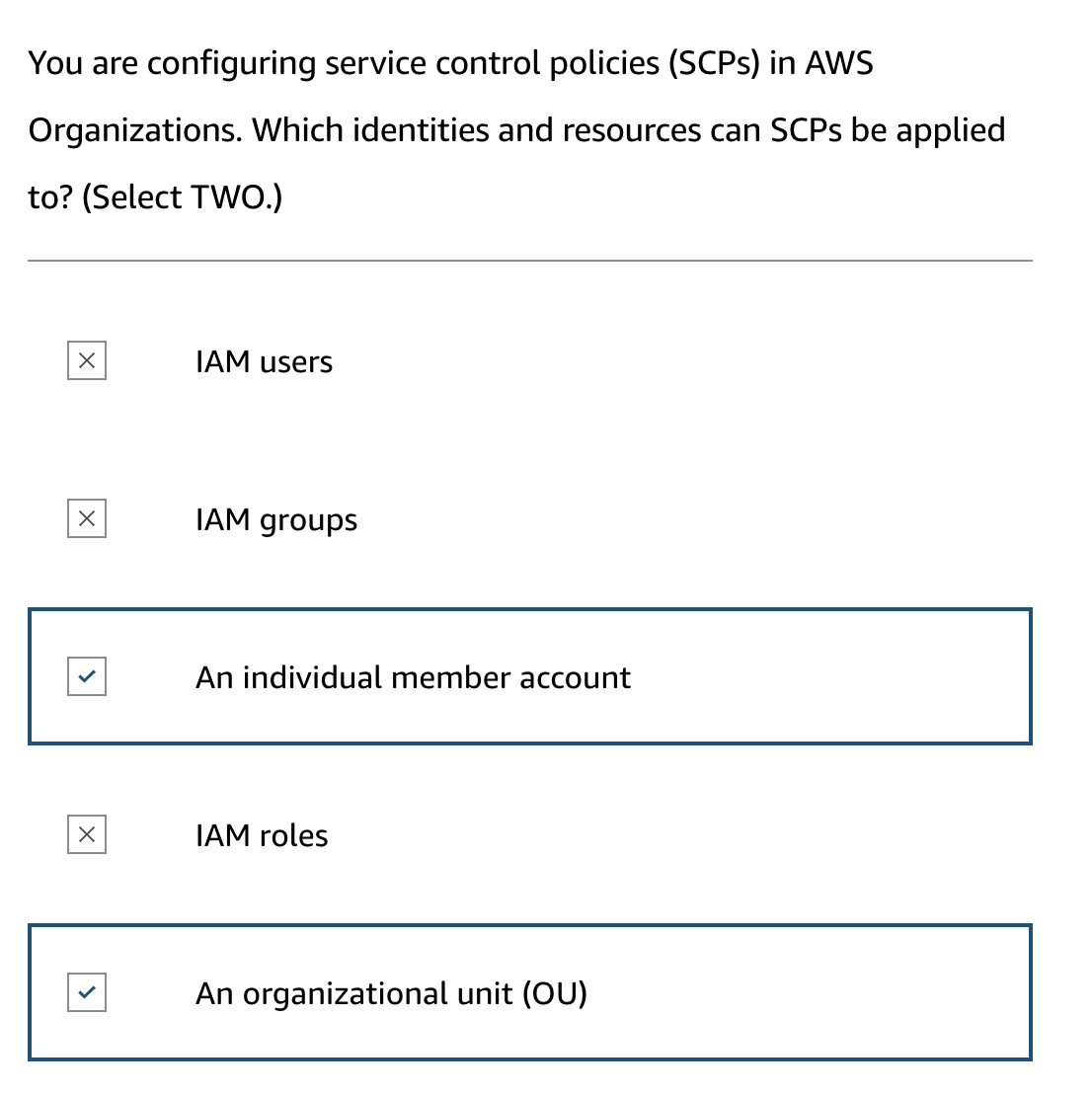
Service Control Policies (SCPs):
- SCPs allow administrators to define and enforce permission limits across the organization.
- These policies determine the AWS services, resources, and API actions that users and roles in member accounts can access.
Using AWS Organizations helps avoid the complexity and potential security risks associated with managing multiple AWS accounts independently, often referred to as an “AWS account spaghetti.” It simplifies access control, billing, and compliance, ensuring a structured and secure cloud environment as companies scale.
Quick Quiz
Compliance and Auditing in AWS
Navigating compliance and auditing in AWS involves understanding the shared responsibilities and utilizing the right tools to ensure that your applications meet industry standards and regulations. This section explains how AWS supports your compliance efforts and what responsibilities fall on you as a user.
Key Points on Compliance in AWS
Industry Standards and Audits:
- Similar to physical businesses (e.g., a coffee shop with health inspections), AWS users must meet applicable regulations like GDPR for EU consumer data, or HIPAA for US healthcare applications.
AWS Compliance Framework:
- Inheritance of Security Practices: AWS provides a secure infrastructure and network following industry best practices, which customers inherit.
- Assurance Programs: AWS complies with numerous assurance programs, reducing the compliance burden for users.
Regional Compliance Considerations:
- Data Residency: Users can choose AWS Regions that comply with specific data residency requirements to meet compliance.
- Data Replication Control: AWS does not replicate data across regions without user permission, aiding in regulatory compliance.
Data Ownership and Control:
- Users retain full control over their data stored in AWS.
- Encryption Flexibility: Various encryption options are available to secure data as per specific standards.
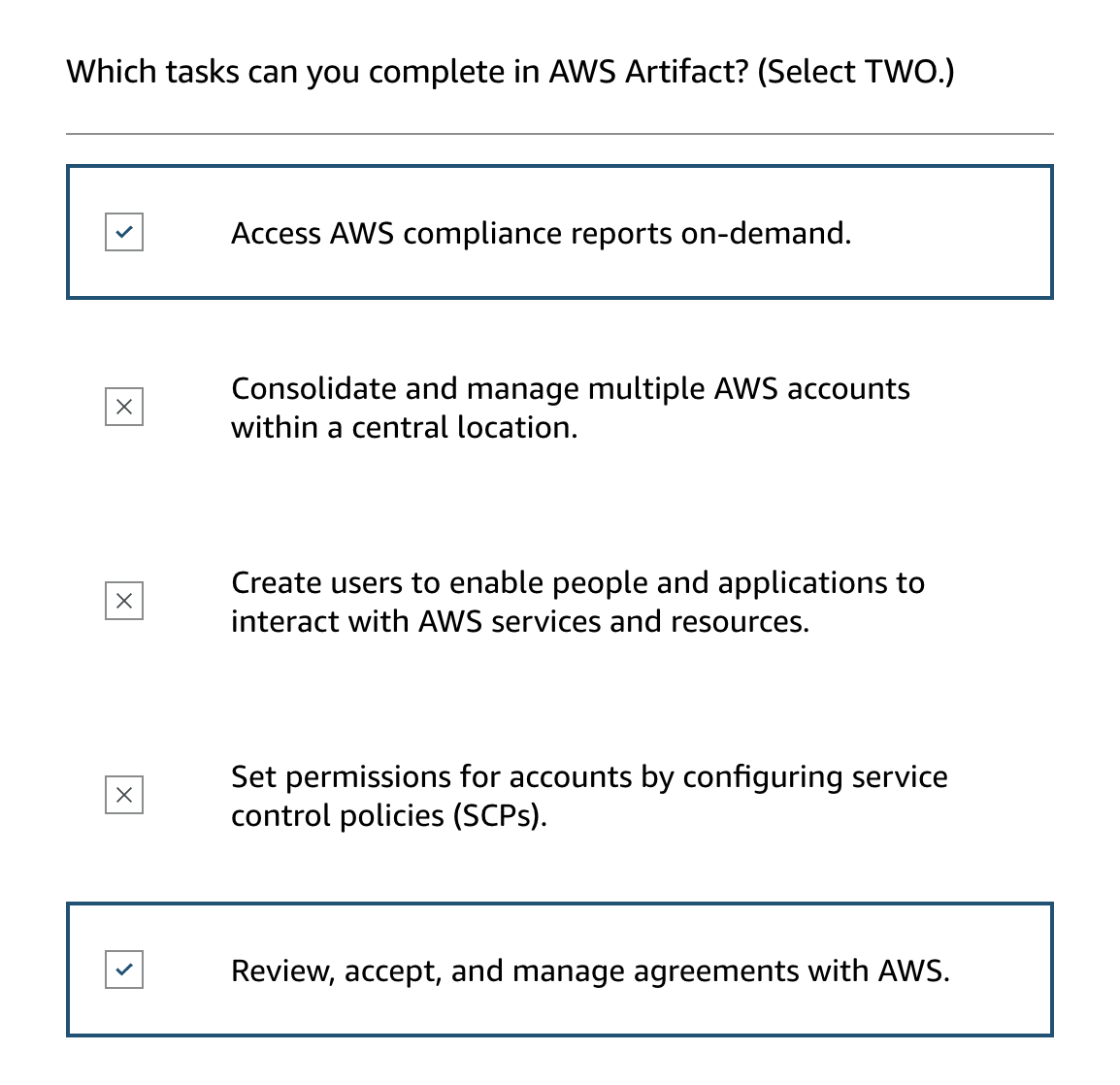
Utilizing AWS Tools and Resources:
- AWS Artifact: Provides access to third-party compliance reports and documentation.
- AWS Compliance Center: Serves as a central hub for finding compliance information and resources, including risk and security whitepapers.
Shared Responsibility Model:
- AWS’s Role: Secures the platform and provides compliance documentation.
- User’s Role: Responsible for securing the applications and data architectures built on AWS.
Conclusion
By understanding and leveraging AWS’s compliance features, while actively managing your responsibilities, you ensure that your applications remain secure and compliant. AWS offers various tools and resources to facilitate compliance with industry standards.
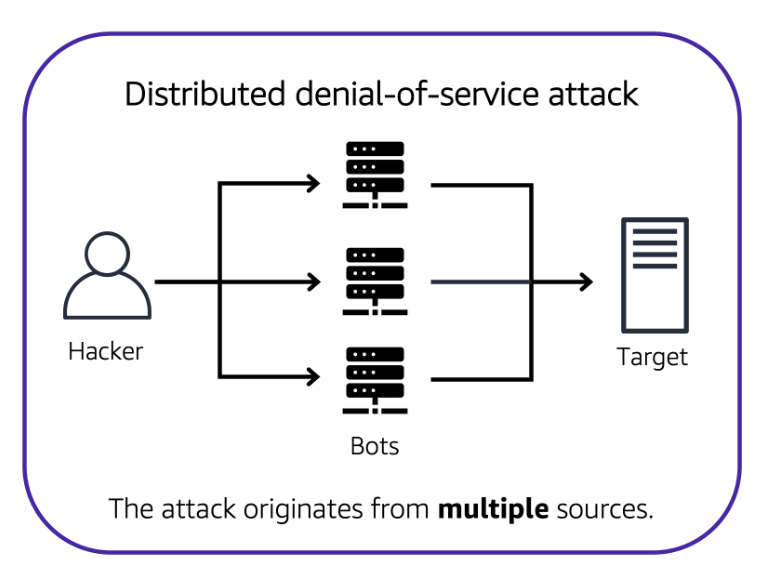
Denial-of-Service Attacks
Distributed Denial of Service (DDoS) attacks aim to overwhelm and incapacitate your applications by flooding them with unwanted traffic. Understanding how to defend against these attacks within AWS is crucial for maintaining service availability and security. Below, we outline the basics of DDoS attacks and the robust defense mechanisms AWS offers to protect your infrastructure.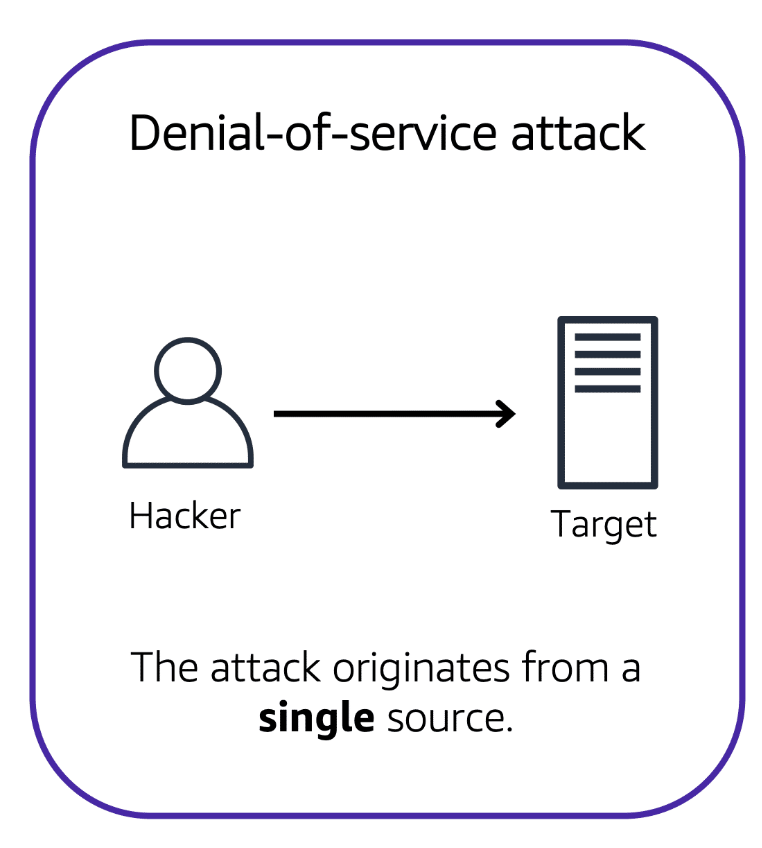
Key Points on DDoS Attacks and AWS Defense Mechanisms
Understanding DDoS Attacks:
- The goal is to disrupt service by overwhelming the application with excessive traffic.
- Attacks use distributed networks of compromised computers (zombie bots) to execute large-scale assaults.
![]()
Examples of DDoS Attacks:
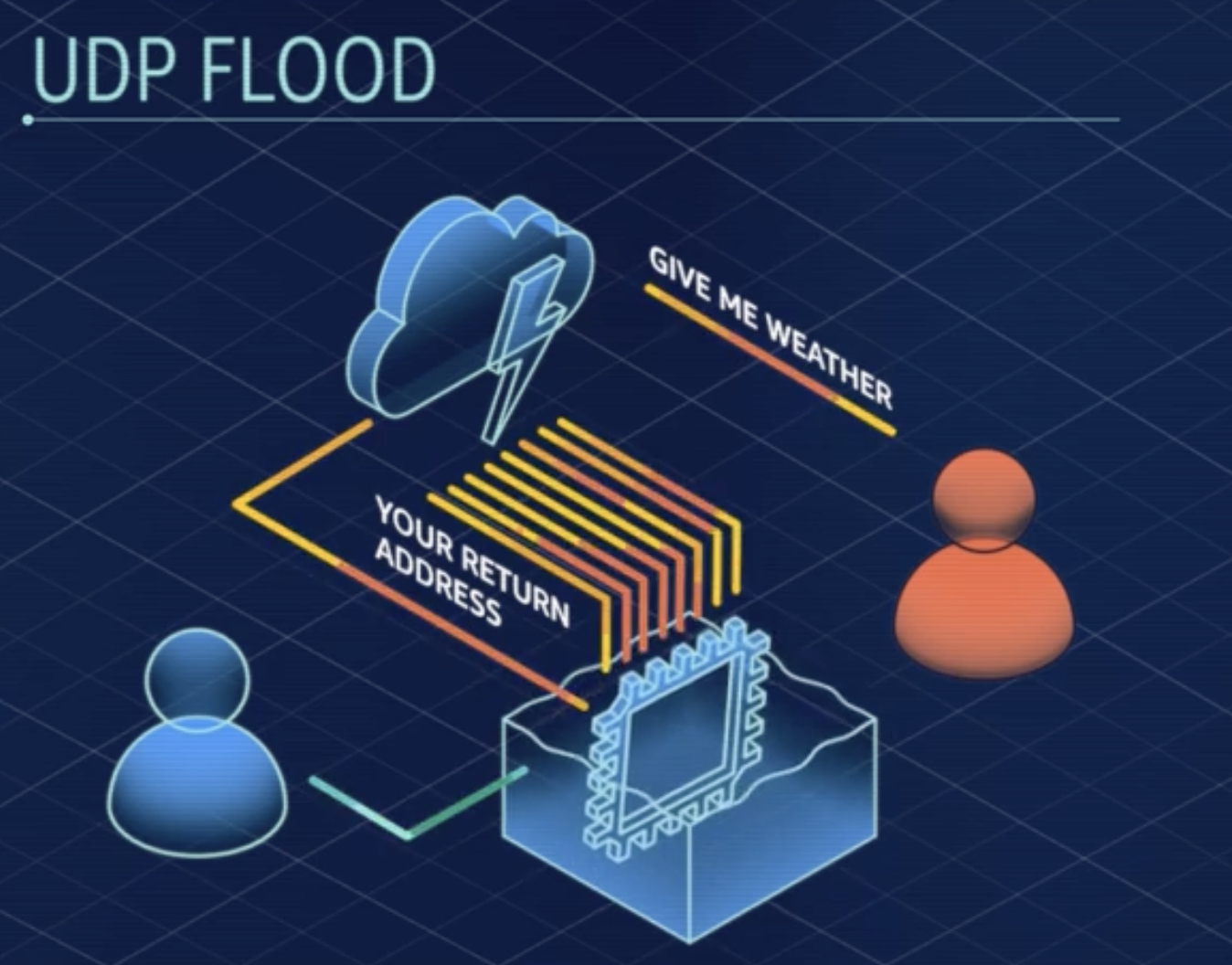
- UDP Flood: Exploits server response to large requests sent to services like the National Weather Service with a spoofed return address.
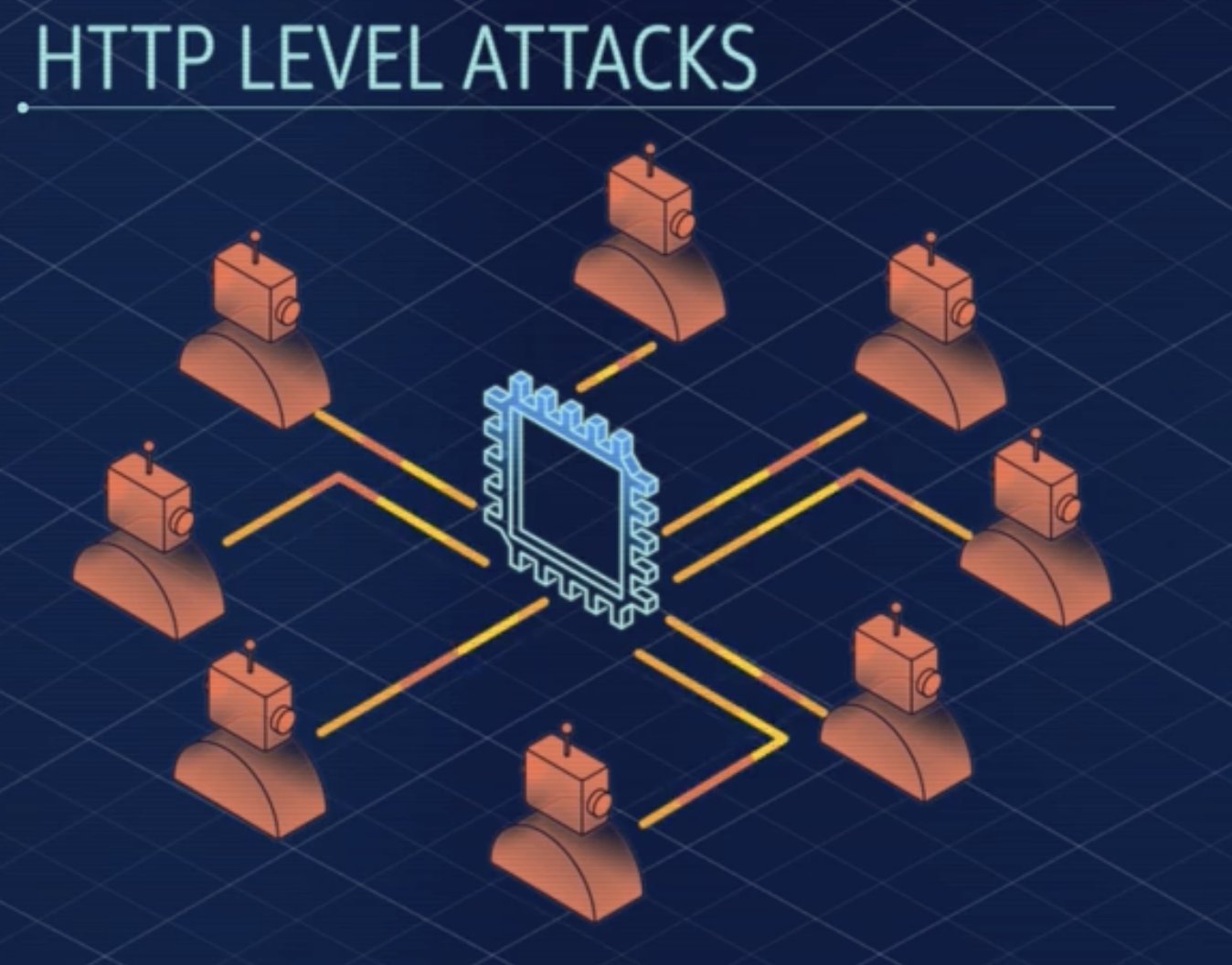
- HTTP Level Attacks: Mimics legitimate user requests in high volumes to block service access to genuine users.
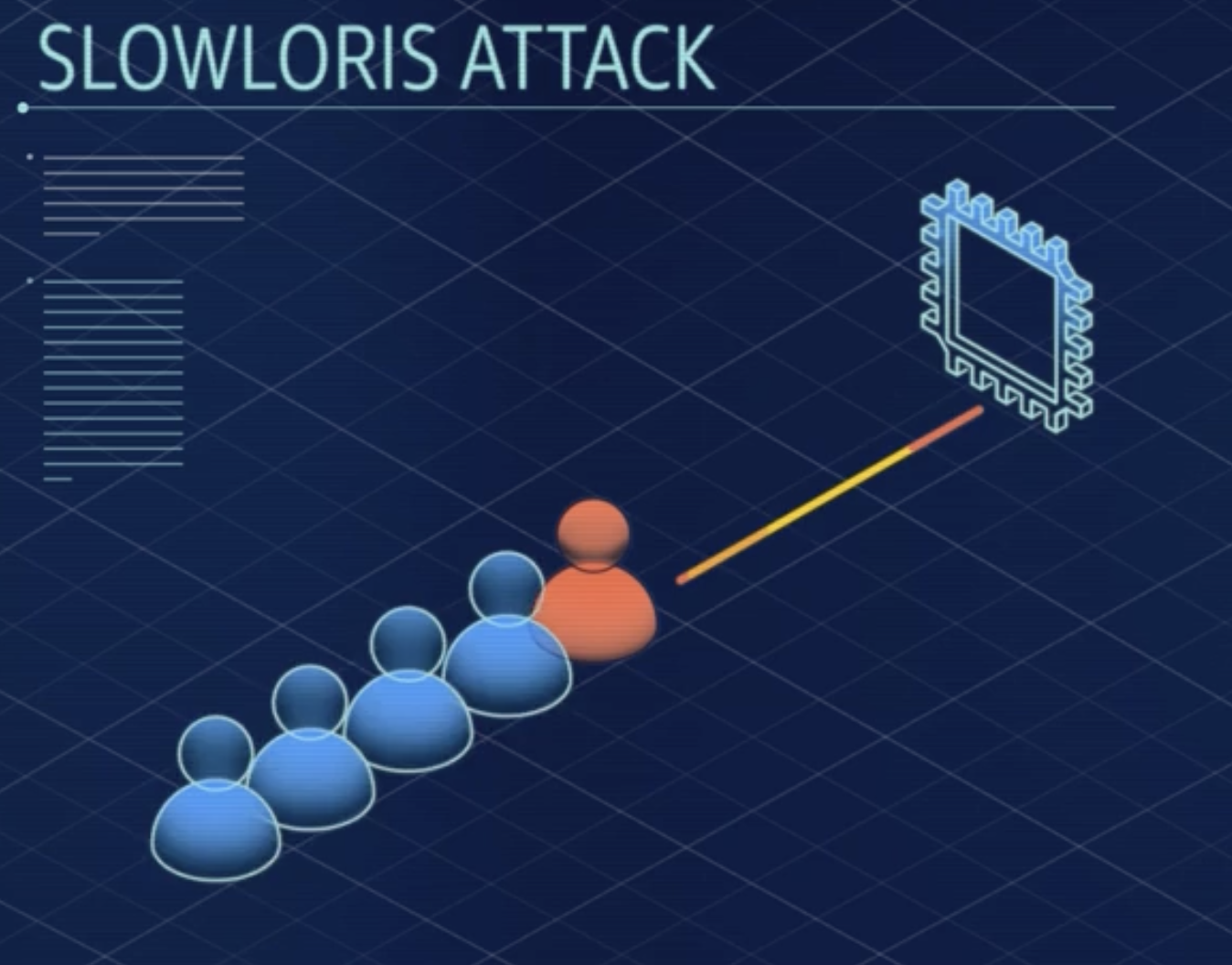
- Slowloris: Simulates a slow connection, occupying server resources for extended periods without completing requests.
- UDP Flood: Exploits server response to large requests sent to services like the National Weather Service with a spoofed return address.
AWS Defense Tools and Strategies:
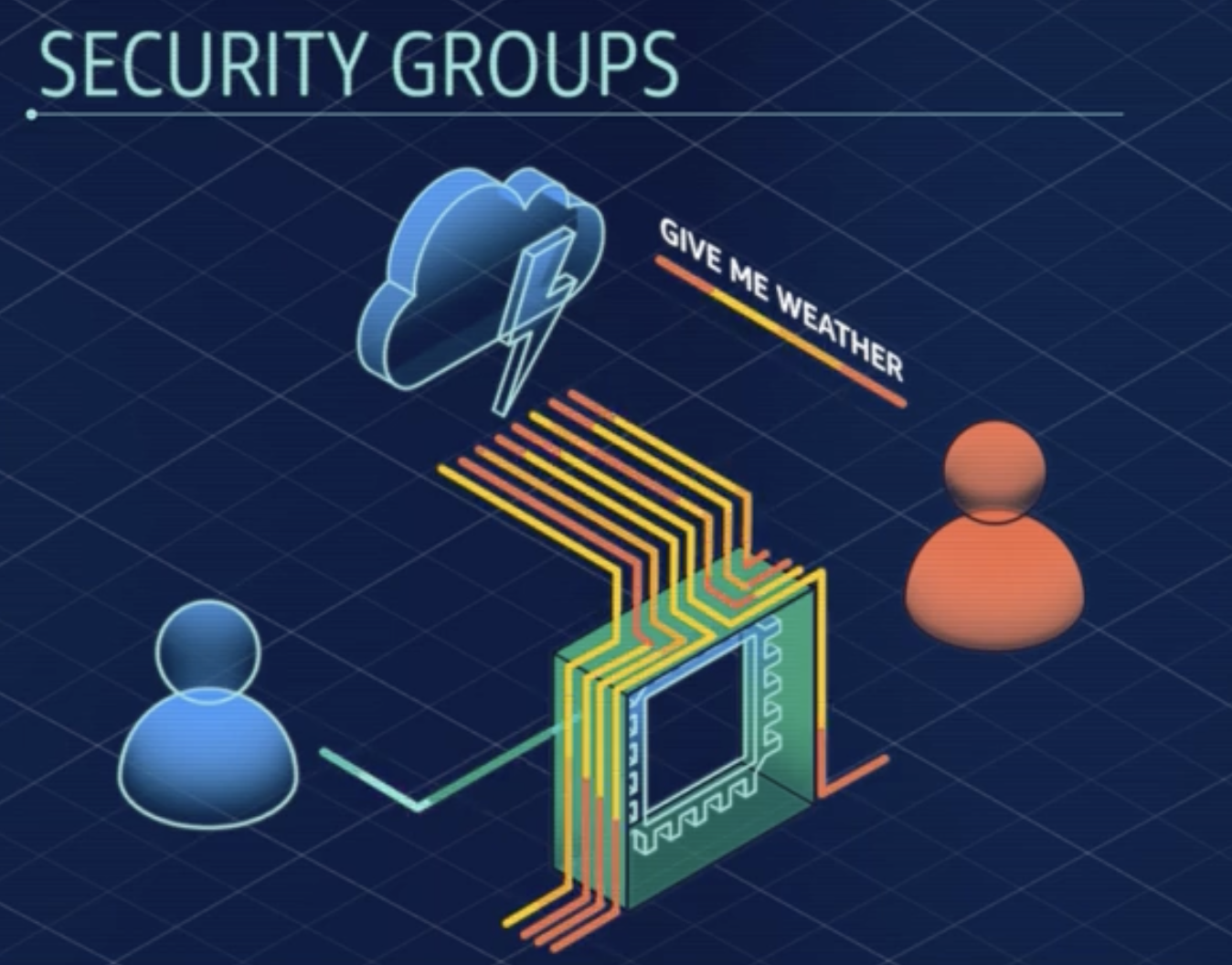
- Security Groups: Filter incoming traffic to allow only legitimate requests, blocking irrelevant protocol traffic at the AWS network level.
- Elastic Load Balancer (ELB): Manages HTTP traffic, ensuring complete requests before passing them to servers, enhancing protection against Slowloris and other similar attacks.
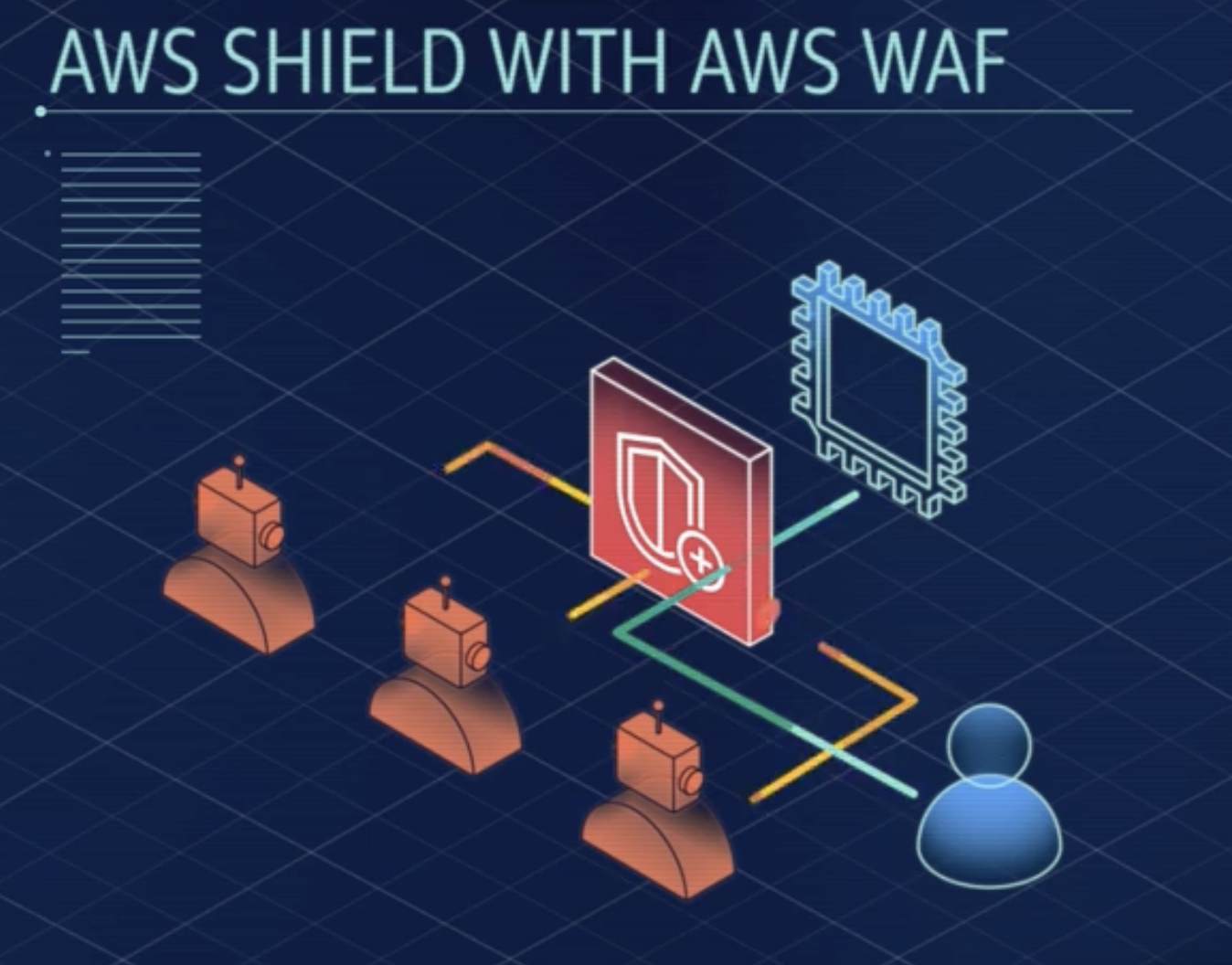
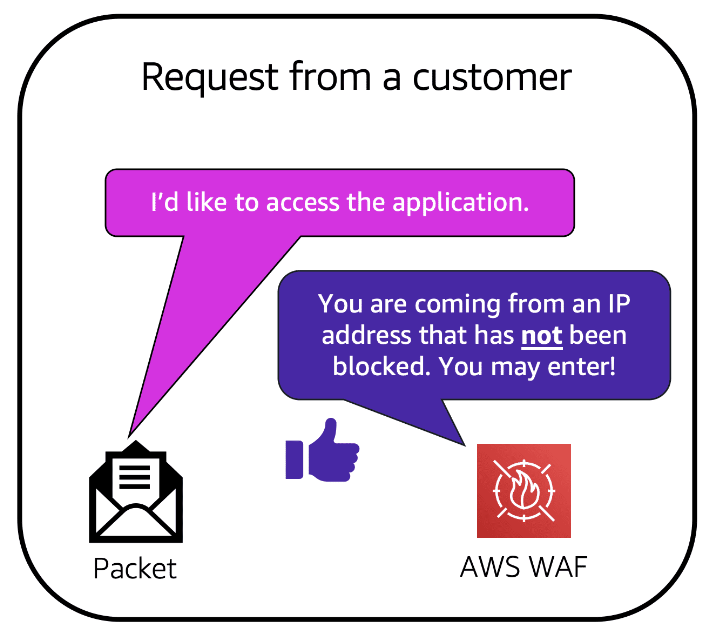
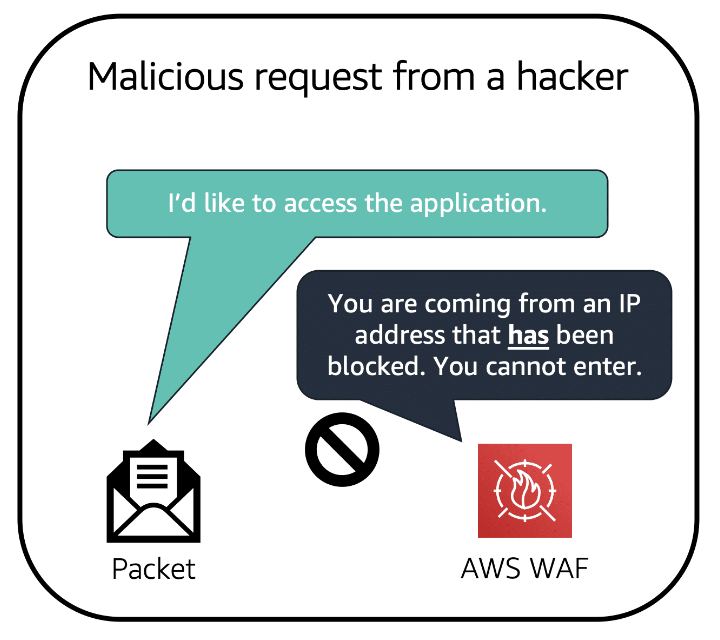
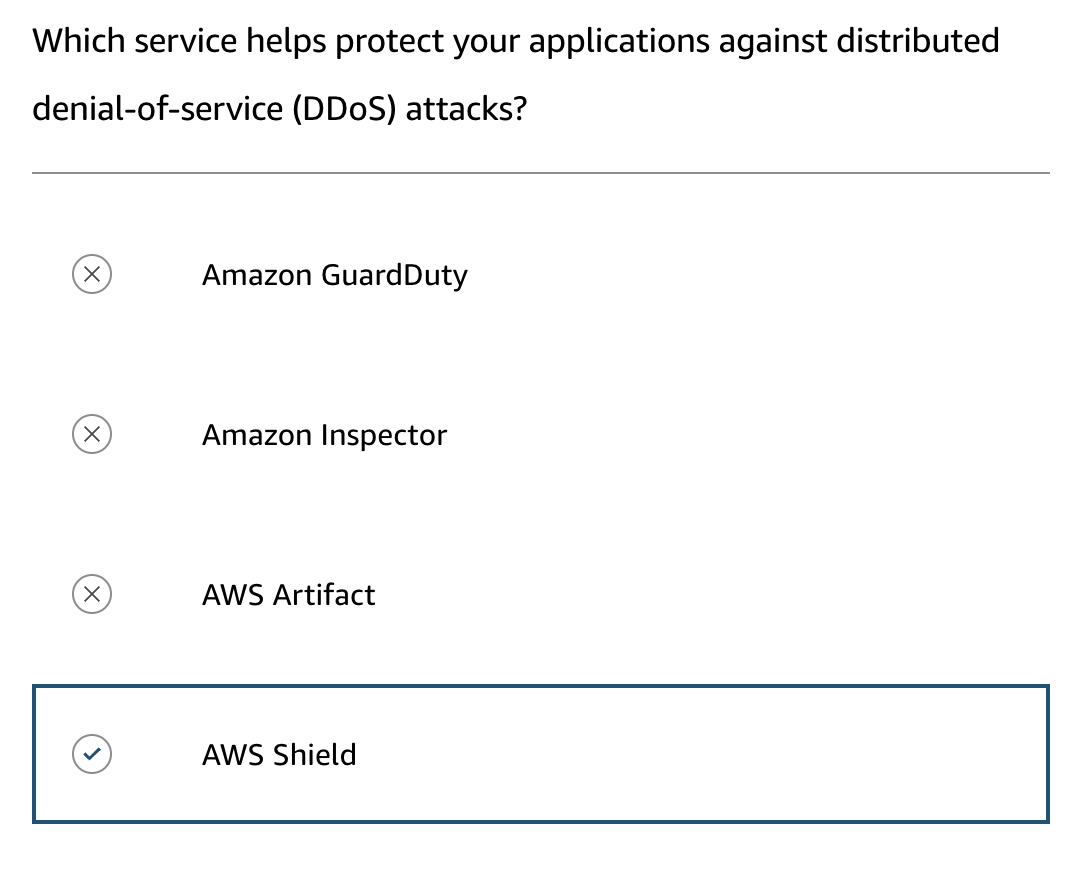
- AWS Shield and AWS WAF: Provide additional layers of security with a web application firewall that detects and blocks malicious traffic based on evolving threat signatures.
- Security Groups: Filter incoming traffic to allow only legitimate requests, blocking irrelevant protocol traffic at the AWS network level.
Advantages of AWS Infrastructure:
- The massive scale of AWS infrastructure provides a natural defense against volume-based attacks, making it financially and logistically challenging for attackers to overwhelm.
- AWS’s comprehensive tools and services are designed not only for functionality but also for robust security against common and sophisticated DDoS attacks.
Conclusion
A well-architected system on AWS, enhanced with specific AWS services like AWS Shield Advanced, offers strong defenses against DDoS attacks, ensuring your applications remain secure and available even under attack.
Additional Security Services
As a business grows, securing data—both at rest and in transit—becomes crucial. AWS offers a robust set of tools and services designed to protect data integrity and prevent unauthorized access, similar to safeguarding physical assets in a coffee shop. Below, we summarize the fundamental AWS security measures that help protect your data effectively.
Key AWS Security Measures
Encryption Fundamentals:
- Encryption at Rest: Ensures data is secure when stored and not actively being accessed or moved.
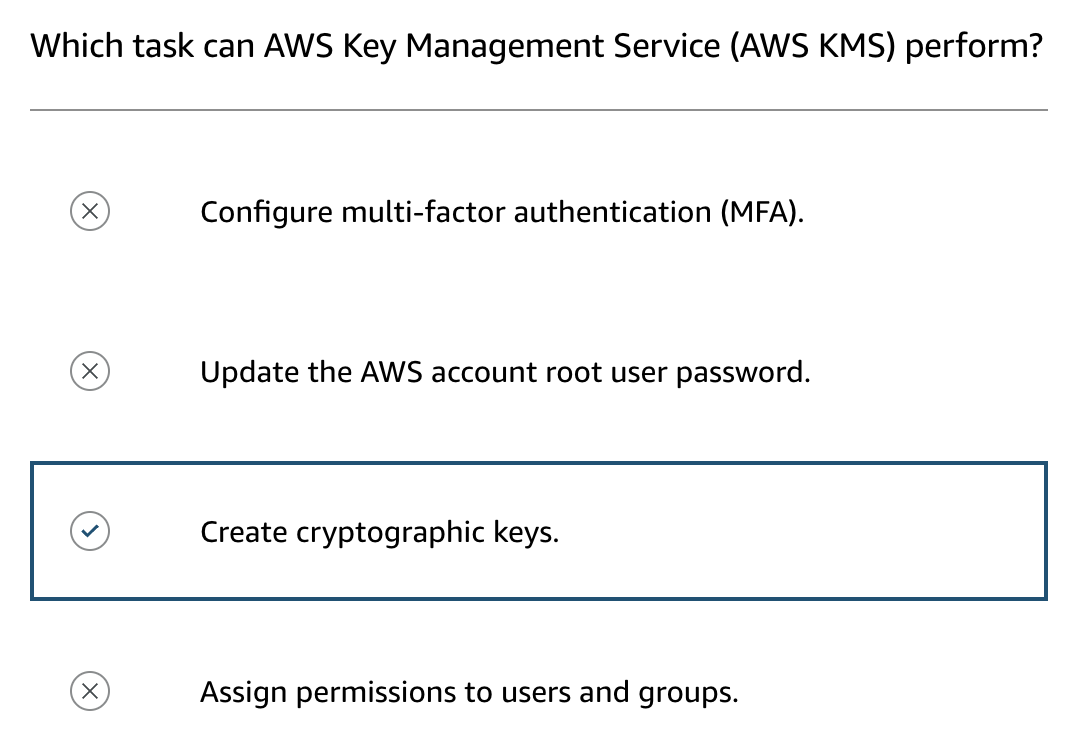
- Example: DynamoDB server-side encryption integrates with AWS Key Management Service (KMS) for secure key management.
- Encryption in Transit: Protects data actively moving from one location to another, ensuring it remains inaccessible to unauthorized users.
- Example: SSL connections and service certificates protect data transfers, such as between an AWS Redshift instance and a SQL client.
- Encryption at Rest: Ensures data is secure when stored and not actively being accessed or moved.
AWS Security Services:
- Amazon Inspector:
- Automates security assessments to check compliance with best practices and identifies vulnerabilities.
- Components include network configuration analysis, an Amazon agent on EC2 instances, and a comprehensive security assessment service.
- Findings are displayed in the Amazon Inspector console and can also be accessed via API for remediation.
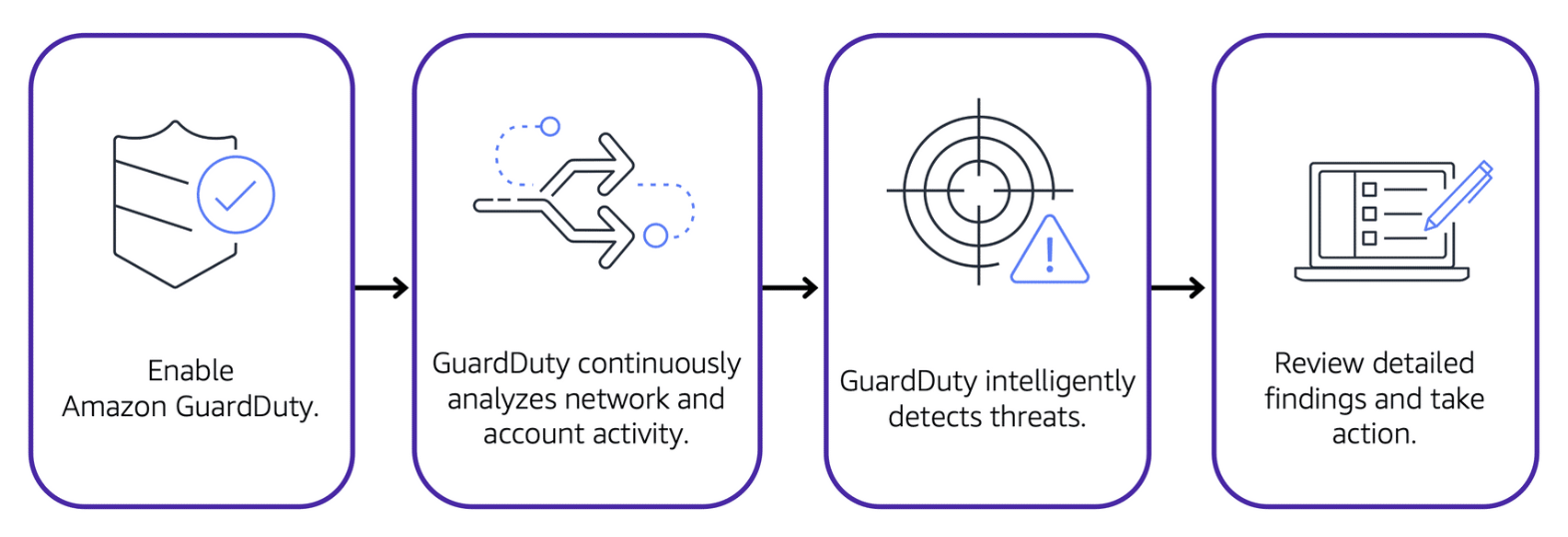
- Amazon GuardDuty:
- Provides threat detection by analyzing metadata from AWS CloudTrail events, Amazon VPC Flow Logs, and DNS logs.
- Utilizes threat intelligence, anomaly detection, and machine learning to identify potential security threats accurately.
- Operates independently of other AWS services, ensuring no impact on performance or availability.
![]()
- Amazon Inspector:
Additional Resources:
- AWS also offers Advanced Shield and Security Hub among other security services.
- Users are encouraged to explore the Resources section for more detailed information on these tools.
Conclusion
AWS provides a comprehensive suite of security tools that mirror the best practices of physical asset protection in a modern digital environment. From encryption techniques that secure data at rest and in transit to sophisticated services like Amazon Inspector and GuardDuty, AWS equips users with the necessary tools to maintain high security and compliance standards.
Summary - AWS Security Management
Security in AWS is underpinned by a shared responsibility model, where AWS secures the cloud infrastructure, and users are responsible for their data and applications. Below is a breakdown of key components and strategies for effectively managing security within AWS.
Key Concepts in AWS Security
Shared Responsibility Model:
- AWS Responsibilities: Secures the cloud infrastructure.
- User Responsibilities: Manages security within the cloud, including data and application security.
Identity and Access Management (IAM):
- Users: Individuals with credentials but no permissions by default.
- Groups: Collections of users.
- Roles: Used to grant temporary permissions and credentials.
- Policies: Define permissions, explicitly allowing or denying actions.
- Identity Federation: Allows integration of corporate identities with AWS, facilitating single sign-on.
- Multi-Factor Authentication (MFA): Particularly recommended for the root user, who has extensive permissions.
AWS Organizations:
- Manages multiple accounts hierarchically.
- Useful for isolating workloads, teams, or applications across different accounts.
Compliance:
- Third-Party Auditors: Verify AWS’s adherence to various compliance programs.
- AWS Compliance Center and AWS Artifact: Provide access to compliance information and documents.
DDoS Protection:
- Tools like Elastic Load Balancing (ELB), Security Groups, AWS Shield, and AWS Web Application Firewall (WAF) help mitigate DDoS attacks.
Encryption:
- Data Ownership: Users own their data and are responsible for its encryption both in transit and at rest.
Security Best Practices
- Adhere to the least privilege principle in IAM.
- Employ encryption consistently for data protection.
- Utilize AWS security services to enhance defense mechanisms.
Conclusion
AWS prioritizes security highly, offering robust tools and guidelines to protect user environments. It is vital for users to understand and implement AWS’s recommended security measures, customize them as per their specific needs, and stay informed via AWS documentation.
Quiz
Reference:
- AWS SkillBuilder CPE Course Module6