Understanding Networking in AWS
The Foundational Role of a VPC in AWS Cloud Networking
A Virtual Private Cloud (VPC) in Amazon Web Services (AWS) serves as the cornerstone of your AWS network infrastructure. It enables you to launch AWS resources in a logically isolated virtual network that you define. This virtual network closely mirrors a traditional network you would operate in your data center, benefiting from the scalability and flexibility of AWS’s cloud infrastructure.
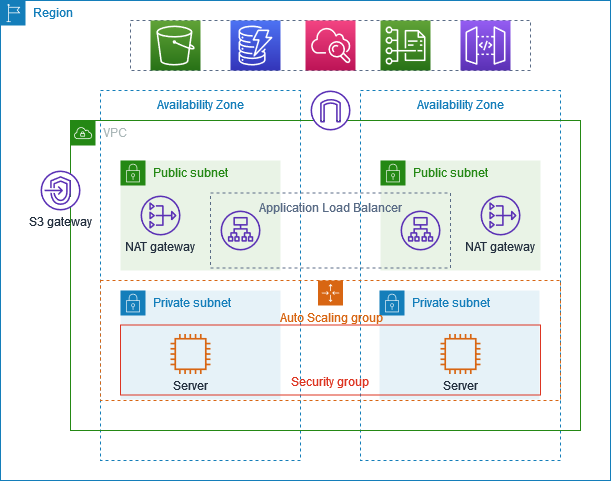
source: https://docs.aws.amazon.com/vpc/latest/userguide/vpc-example-private-subnets-nat.html
Key Components and Concepts of VPC
1. Subnets:
- Subnets are subdivisions within your VPC, each representing a range of IP addresses within the VPC. They help organize and isolate resources within different availability zones for high availability.
2. Internet Gateway:
- An Internet Gateway is a horizontally scaled, redundant, and highly available VPC component that allows communication between instances in your VPC and the internet. It serves as a target in your VPC route tables for internet-routable traffic.
3. Route Tables:
- Route tables contain a set of rules, called routes, that determine where network traffic is directed. Each subnet in your VPC must be associated with a route table, which controls the routing for the subnet.
4. Security Groups:
- Security Groups act as virtual firewalls for your instances to control inbound and outbound traffic. They are stateful, meaning they track the state of network connections passing through them, allowing responses to outbound traffic automatically.
5. Network ACLs (Access Control Lists):
- Network ACLs provide an additional layer of security at the subnet level, controlling inbound and outbound traffic to and from subnets. Unlike security groups, network ACLs are stateless, meaning they evaluate each packet that crosses the subnet boundary.
6. VPC Peering:
- VPC Peering allows you to route traffic between VPCs using private IP addresses, facilitating communication between VPCs in the same or different AWS accounts and regions.
7. Transit Gateway:
- AWS Transit Gateway acts as a central hub to connect multiple VPCs and on-premises networks. It simplifies network management by consolidating and controlling the routing between these environments.
8. AWS PrivateLink:
- AWS PrivateLink enables private connectivity between VPCs, AWS services, and on-premises applications without exposing traffic to the public internet. This enhances security by keeping traffic within the AWS network.
Connecting Your AWS Networking Environment to the Internet
To connect your VPC to the internet, you need to:
1. Attach an Internet Gateway:
- Attach an Internet Gateway to your VPC. This provides a target for internet-bound traffic from instances within your VPC.
2. Update Route Tables:
- Add routes to your route tables that direct internet-bound traffic to the Internet Gateway.
3. Assign Public IP Addresses:
- Ensure that instances that need to communicate with the internet have public IP addresses or Elastic IP addresses.
4. Configure Security Groups and Network ACLs:
- Modify the inbound and outbound rules of your security groups and network ACLs to allow the necessary traffic to flow to and from the internet.
Isolating Resources Within Your AWS Networking Environment
Isolation of resources within your AWS networking environment can be achieved through several strategies:
1. Subnets:
- Create public and private subnets to separate resources that need direct internet access from those that don’t. For example, public subnets can house web servers, while private subnets can house database servers.
2. Security Groups:
- Configure security groups to control traffic to and from specific instances based on IP address, protocol, and port.
3. Network ACLs:
- Use network ACLs to provide an additional layer of stateless traffic filtering at the subnet level.
4. VPC Peering and Transit Gateways:
- Use VPC Peering or Transit Gateways to connect isolated VPCs while maintaining control over the traffic flow between them.
Creating a VPC with Subnets, an Internet Gateway, Route Tables, and Security Groups
Here is a step-by-step outline to create a VPC and configure its components:
1. Create a VPC:
- Define your VPC with a specified IPv4 CIDR block.
2. Create Subnets:
- Create public and private subnets within different availability zones to enhance fault tolerance.
3. Attach an Internet Gateway:
- Attach an Internet Gateway to your VPC to allow internet access.
4. Update Route Tables:
- Create route tables and associate them with your subnets. Add a route in the public subnet’s route table to direct internet-bound traffic to the Internet Gateway.
5. Configure Security Groups:
- Create and configure security groups to control inbound and outbound traffic to your instances. For example, allow HTTP and HTTPS traffic for web servers, and limit SSH access to specific IP addresses.
6. Deploy Instances:
- Launch EC2 instances within your subnets, applying the appropriate security groups and configuring their IP addresses as needed.
By following these steps and understanding these concepts, you can effectively set up and manage a secure and scalable networking environment in AWS.
References
- AWS Documentation on Amazon VPC.
- Example: VPC with servers in private subnets and NAT
